3 Steps to Securing FTP on IIS 8
The FTP protocol is some 43 years old now. Yet it continues to be one of the most widely used file transfer technologies available. Over the years it has been shown to be vulnerable to brute force attacks, packet capture, and other attack vectors. Fortunately with IIS 8 on Windows Server 2012 your FTP server doesn’t have to be vulnerable. It goes without saying that FTP Authentication and Authorization are the most fundamental methods to secure your server. Here are three additional things you can do to increase the security of your server’s FTP service and minimize its attack footprint.
IIS 8 FTP Logon Attempt Restrictions
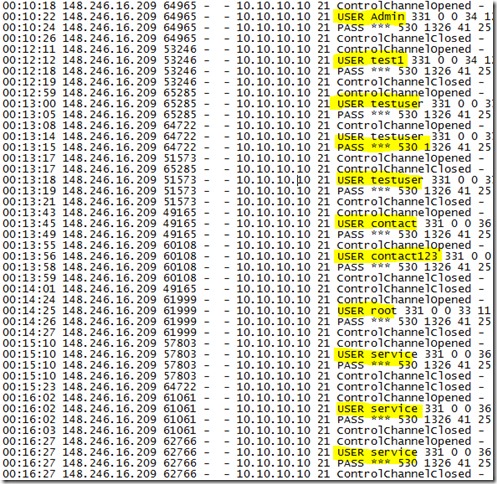
One of the most common FTP attack vectors is the dictionary attack. Using automated tools hackers will repeatedly hammer your FTP site with thousands of username and password combinations hoping to find that one account with an easy password. In the picture below you can see just a snippet of this automated activity. Fortunately none of these attempts were successful.
IIS 8 now features FTP Logon Attempt Restrictions. This powerful feature is not available in IIS 7 or IIS 7.5. Once configured automated logon attacks will be stopped in their tracks. From IIS Manager simply click on FTP Logon Attempt Restrictions.
Configuring the FTP Logon Attempt Restrictions module is easy. Simply choose how many logon attempts are to be allowed and the time period for them to occur. When you consider that most FTP clients will save passwords in a profile, legitimate users on your FTP site should only need 1-2 logon attempts. However, depending on how many FTP users you’re hosting and their technical savvy you may need to tweak these settings.
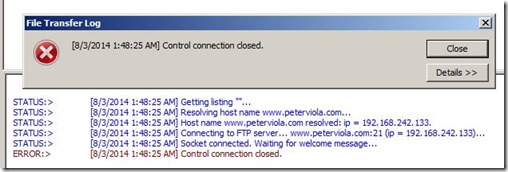
Testing my FTP site now with the new logon attempt restrictions it is easy to see how well it works. After the threshold is exceeded my connection to the server is forcibly closed. Automated hack attempts will no longer be a threat to this FTP server.
Enable FTP Over SSL with IIS 8
The FTP protocol wasn’t originally designed for encryption. Fortunately with IIS 8 (and IIS 7) your FTP sessions can now be encrypted with SSL. To configure FTPS also known as FTP Over SSL open IIS Manager. You can either specify using SSL when adding FTP Publishing to a site or alternatively just going to the FTP SSL Settings on an existing site. Connecting with SSL can either be optional or or you can force all connections to use it. Using the drop down menu choose the certificate that you want to be used to encrypt the connections. Windows Server 2012 has a default certificate available however you are also welcome to install your own 3rd party certificate.
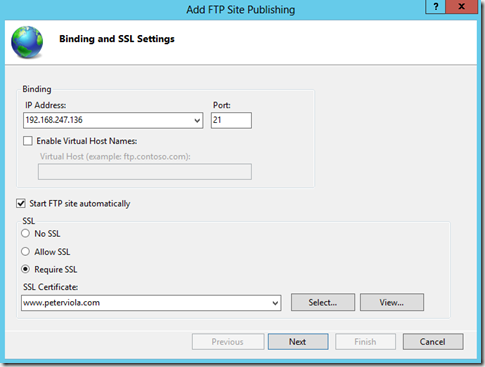
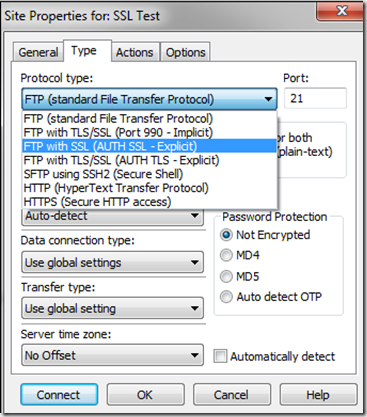
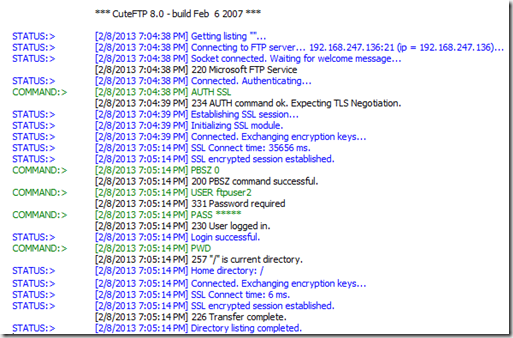
After you’ve configured the SSL settings on the server you just need to change your FTP client connection properties. In the picture below I’m using a legacy version of Cute FTP 8.0. Depending on which FTP client you’re using your protocol menu will look different.
Having changed my FTP client settings I attempt to connect to the server using SSL. The first time you connect to the server you will be prompted to accept the new SSL certificate. The log snippet below shows that my FTP session is being properly established with SSL. My communication with the server is now secure and protected. Here is a more detailed walk through of configuring FTP over SSL on IIS 8.
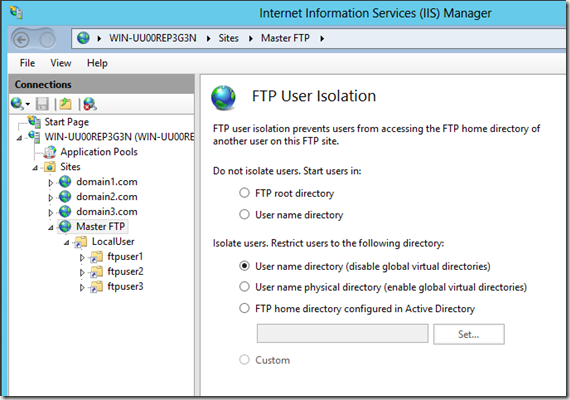
Configuring IIS 8 FTP User Isolation
When IIS 7 was released the FTP service had been completely redesigned from the ground up with security in mind. This was a welcome change indeed from IIS 6. In addition to supporting FTP over SSL it introduced FTP User Isolation. Multiple users on the same FTP site could be separated regardless of which file path they were being logged into without risk of someone traversing up parent paths to other user folders.
The FTP Authorization rules make it easy to identify multiple users or even local groups to have access to the FTP server. The user isolation is accomplished by creating a virtual directory called LocalUser and then choosing User name directory (disable global virtual directories). The LocalUser virtual directory should point to the FTP root directory and then you create a separate virtual directory for each FTP user which points to their destination path.
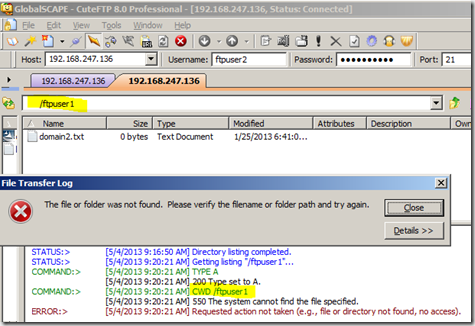
With FTP User Isolation configured your users will never be able to move up up to a parent path beyond their individual root directory. Even if a user were able to correctly guess the username and virtual path of another FTP account on the server they will not be able to reach it. Due to the confines of the isolation the FTP session can not see anything else on the server. In the example below I login with local account ftpuser2 and attempt to change the path to /ftpuser1 however that path does not exist and therefore is not accessible to my user. Here is a more detailed walkthrough of configuring FTP User Isolation on IIS 8.
In Summary
IIS 8 on Windows Server 2012 offers the most secure FTP service of any IIS version to date. You have multiple layers of FTP security available by leveraging FTP Logon Attempt Restrictions, FTP Over SSL, and FTP User Isolation. Your FTP server will be well protected using these built-in modules. With internet security there is no ‘patch’ for complacence. More security is always better so implement it when it’s readily available to you. Thanks for reading.