Preventing Automated Attacks with IIS Dynamic IP Restrictions
Another one of the great built-in features of IIS 8 is Dynamic IP Restrictions (DIPR). With a few simple configuration steps you can quickly set limits for blocking IP addresses based on the number of concurrent requests or frequency of requests over a period time. With these parameters in place IIS will take over blocking requests unattended thereby making your server more secure.
Before DIPR was available on IIS 7 you could manually block 1 IP or a range of IPs easily in the IP Address and Domain Restrictions module. However this could be a time consuming task if your server was under attack. Using a tool like Log Parser to examine the site’s logs you could identify IPs with suspicious activity but then you still had manually enter Deny Rules. Determined hackers will use a variety of IPs from proxy servers so by the time you’ve blocked a handful a new range could be starting up. DIPR was released out-of-band for IIS 7 and IIS 7.5 so you can leverage this great security tool on those web servers as well. In this walk through I cover how to configure Dynamic IP Restrictions and even show a test in action.
Installing Dynamic IP Restrictions
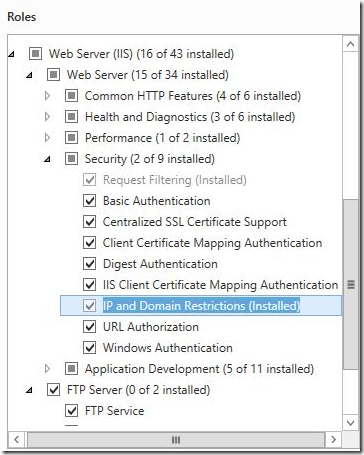
Open the Server Manager and to Web Server role. Under Security ensure that IP and Domain Restrictions is installed.
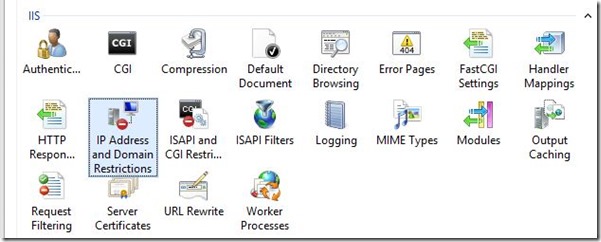
IP Address and Domain Restrictions in IIS Manager
Open IIS Manager and click on IP Address and Domain Restrictions.
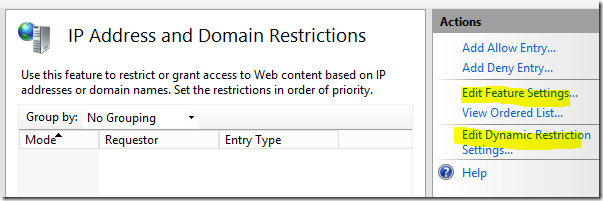
From this window you can either Add Allow Entry rules or Add Deny Entry rules. These rules would be for manually blocking (or allowing) one IP address or an IP address range. You have to be care when blocking an IP range because you could inadvertently block legitimate traffic. Click on Edit Dynamic Restriction Settings to set the dynamic thresholds for blocking IP addresses.
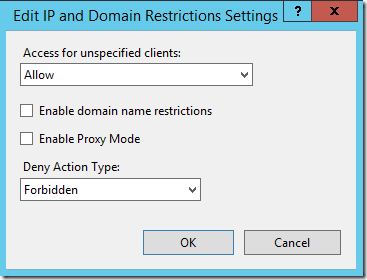
Click Edit Feature Settings to set the Deny Action Type. In this example I’ve set Forbidden so blocked requests will receive an http 403 status error. These errors will also be recorded in the site’s log for us to review later.
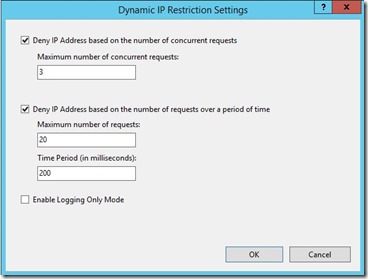
On the Dynamic IP Restriction Settings screen you can choose the maximum number of concurrent requests to block. And you can also Deny IP addresses based on frequency of requests over a period of time.
As always depending on the volume of your web site’s traffic you should test these settings to ensure that legitimate traffic does not get blocked.
Testing Dynamic IP Address Blocking
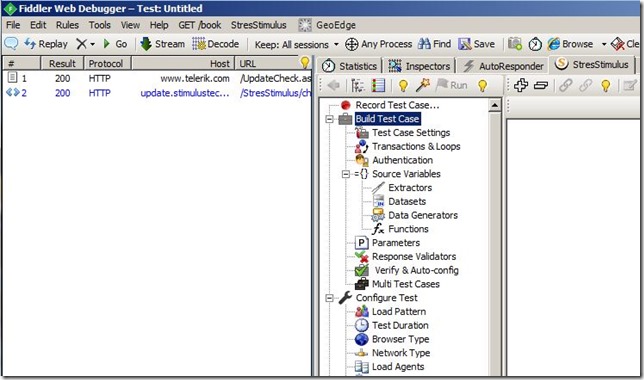
I didn’t have a real security incident available for testing the DIPR module so I did the next best thing. Using Fiddler the free debugging tool from Telerik and StressStimulus a free load testing plugin from StimulusTechnology I hammered my test virtual server for a few minutes and got the desired results. With Fiddler open you will see the StressStimulus module. From here you can record your test case or open an existing test case as well as edit the test case paramters.
Test Results
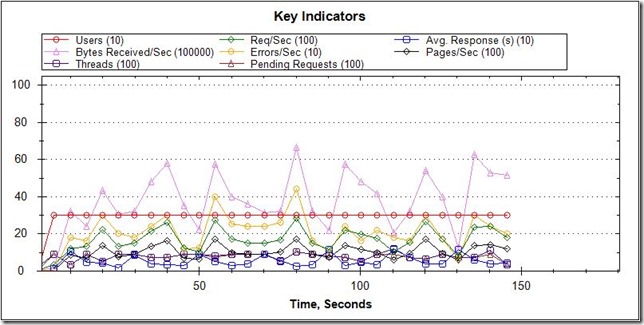
StressStimulus gives you multiple detailed charts to review to gauge the performance of your site and identify potential areas of weakness. For my test I choose to hit the wp-login.php page on my test WordPress site with 3 concurrent requests and 100 iterations. The test completed within a few minutes.
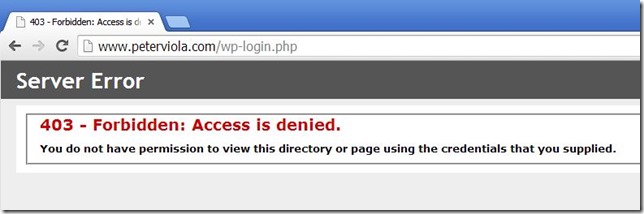
Visiting the test page from the server running StressStimulus I get the expected result. It’s blocked by a 403 error. The full description of this code is 403.502 – Forbidden: Too many requests from the same client IP; Dynamic IP.
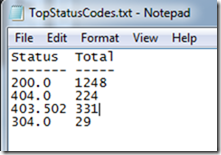
Using the Log Parser query below to analyze the site log I see that 331 requests were blocked with a 403.502 status code.
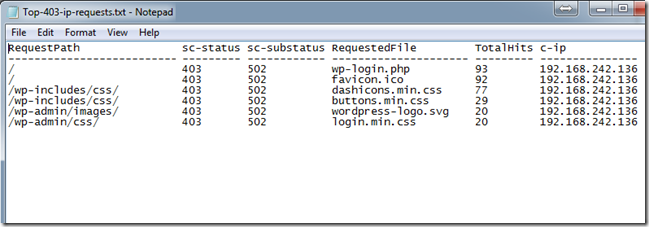
SELECT TOP 100 STRCAT(EXTRACT_PATH(cs-uri-stem),'/') AS RequestPath, sc-status,sc-substatus, EXTRACT_FILENAME(cs-uri-stem) AS RequestedFile, COUNT(*) AS TotalHits, c-ip FROM w3svc.og TO top-403-ip-requests GROUP BY cs-uri-stem, sc-status,sc-substatus,c-ip ORDER BY TotalHits DESC
Further examination of the log with Log Parser shows the full break down of the requests blocked with 403 status.
SELECT TOP 100
STRCAT(EXTRACT_PATH(cs-uri-stem),’/') AS RequestPath, sc-status,sc-substatus,
EXTRACT_FILENAME(cs-uri-stem) AS RequestedFile,
COUNT(*) AS TotalHits, c-ip
FROM w3svc.og TO top-403-ip-requests
where sc-status=403
GROUP BY cs-uri-stem, sc-status,sc-substatus,c-ip
ORDER BY TotalHits DESC
Summary
The Dynamic IP Restrictions module is available with IIS 8 as well as IIS 7 and IIS 7.5. It is a powerful tool to block automated attacks on your site and requires minimal configuration and maintenance. Thanks for reading.